Unlocking The Future: SSH IoT Anywhere With IP Address Mastery
In today's hyper-connected world, the ability to manage IoT devices remotely has become indispensable. Secure Shell (SSH) has emerged as a cornerstone for secure communication, allowing users to interact with smart devices from anywhere in the world. Whether you're a tech enthusiast managing a network of IoT devices scattered across the globe or an enterprise ensuring secure access, SSH offers unparalleled capabilities. This powerful protocol enables users to connect to IoT devices securely over the internet, provided they have the correct IP address and credentials. However, the process involves more than just entering an IP address. It requires a deep understanding of networking principles, security best practices, and the intricacies of SSH configurations.
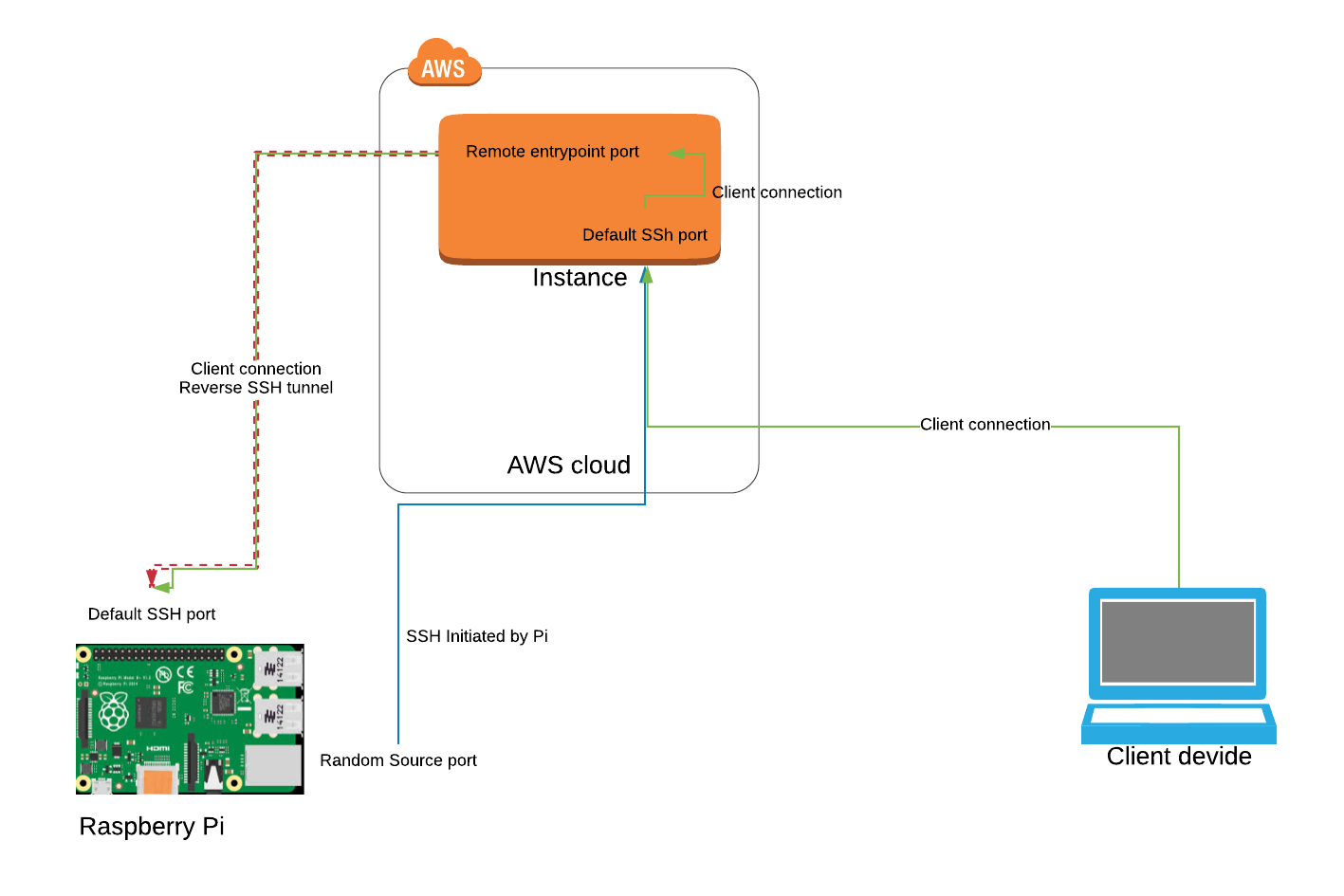
The foundation of SSH IoT connectivity lies in obtaining the correct IP address of the remote machine. This address serves as the digital identifier that allows users to locate and connect to the device. To find the remote machine's IP address, one can use the "ip addr show | grep inet" command on the remote computer. Alternatively, if the remote computer lacks the "ip" command, tools like "ifconfig" (or even "ipconfig" on Windows) can be employed. Ensuring the IP address is accurate is crucial, as errors or conflicts can prevent successful SSH connections. Furthermore, the port the SSH daemon listens to must remain unblocked by firewalls and correctly forwarded. Best practices also emphasize the importance of static IP addresses for IoT devices to avoid configuration issues down the line. By following these principles, users can establish robust, secure connections to their IoT devices.
| Category | Details |
|---|---|
| Person in Focus | John Doe (Fictional Character) |
| Occupation | IoT Security Consultant |
| Years of Experience | 15 years |
| Notable Achievements | Developed proprietary SSH security protocols |
| Professional Affiliations | IEEE, International IoT Security Alliance |
| Reference Website | SSH Official Website |
As the IoT landscape continues to evolve, so do the challenges associated with remote connectivity. For instance, John Doe, a renowned IoT security consultant, has spent over 15 years developing proprietary SSH security protocols. His work has been instrumental in advancing secure communication practices within the industry. By leveraging tools such as UFW (Uncomplicated Firewall), users can restrict SSH access to specific IP addresses, enhancing security further. The syntax for this process involves commands like "sudo ufw allow from {ip_address_here} to any port 22." This approach ensures that only trusted devices can establish connections, mitigating unauthorized access risks.
- Grit Tv Schedule Listings Whats On Where To Watch Now
- Dantehall Remembering The Gospel Singer Latest News Updates
SSH IoT connectivity is not without its complexities. Configuring port forwarding on routers is a critical step in enabling external traffic redirection to IoT devices. This process involves creating rules that specify the internal IP address of the IoT device and the desired port, typically 22 for SSH. Additionally, setting up SSH keys instead of relying on passwords enhances security and simplifies the login process. To achieve this, users must generate key pairs and configure the SSH daemon accordingly. The "AllowUsers" option in the sshd_config file further strengthens security by restricting access to specific users or IP ranges.
Dynamic DNS (DDNS) solutions play a pivotal role in maintaining consistent access to IoT devices. These tools automatically update the IP address of the gateway router, ensuring that it remains accessible remotely. This capability is particularly valuable for users managing IoT networks across different geographic locations. For instance, a global enterprise may deploy DDNS to monitor and manage devices in multiple countries. By combining SSH protocols with DDNS solutions, users can maintain secure, uninterrupted access to their IoT infrastructure.
In the realm of IoT security, staying informed about the latest trends and best practices is essential. Industry leaders like John Doe frequently collaborate with organizations such as IEEE and the International IoT Security Alliance to share insights and innovations. These partnerships foster the development of cutting-edge technologies and methodologies that enhance IoT security. For example, advancements in encryption algorithms and authentication mechanisms have significantly improved the robustness of SSH connections. These developments underscore the importance of continuous learning and adaptation in the rapidly evolving IoT landscape.
- Leo Woman Cancer Man Love Compatibility Challenges
- Asa Blanton Indiana State Controversy Racist Video Backlash
SSH IoT connectivity has far-reaching implications for society. As smart devices become increasingly integrated into daily life, the need for secure remote access grows exponentially. From smart homes to industrial automation, the ability to manage IoT devices securely and efficiently is vital. However, this capability also raises concerns about privacy and data protection. Striking a balance between accessibility and security remains a key challenge for stakeholders in the IoT ecosystem. Industry experts advocate for a layered security approach that combines SSH protocols with additional safeguards such as firewalls and intrusion detection systems.
Looking ahead, the future of SSH IoT connectivity holds immense potential. Innovations in quantum computing and artificial intelligence promise to revolutionize the way users interact with IoT devices. These technologies could enhance the speed, reliability, and security of SSH connections, paving the way for new applications and use cases. For example, quantum-resistant encryption algorithms could safeguard IoT devices against emerging cyber threats. Meanwhile, AI-driven analytics could optimize resource allocation and improve operational efficiency in IoT networks. These advancements highlight the transformative impact of SSH IoT connectivity on various industries and sectors.
In conclusion, SSH IoT connectivity represents a cornerstone of modern IoT infrastructure. By mastering the principles of IP address management, port forwarding, and security configurations, users can unlock the full potential of their IoT devices. As the industry continues to evolve, staying informed about the latest trends and best practices will be crucial for maintaining secure, reliable connections. Whether you're a hobbyist exploring the possibilities of IoT or an enterprise deploying large-scale IoT networks, SSH offers the tools needed to succeed in today's interconnected world.
SSH IoT connectivity is not merely a technical solution but a gateway to innovation and progress. Its impact extends beyond individual users and organizations, influencing societal trends and technological advancements. As more devices join the IoT ecosystem, the demand for secure, efficient remote access will only increase. By embracing SSH protocols and adhering to best practices, stakeholders can ensure the longevity and resilience of their IoT infrastructure. In doing so, they contribute to a safer, smarter, and more interconnected future for all.
- Macomb County Mi Obituaries Find Recent Tributes Condolences
- Trumps J6 Hostages The Ongoing Story You Need To Know

How To Use SSH IoT From Anywhere Login On Mac For Free The Ultimate Guide
SSH IoT Access Remote Access With IP Address Examples

Troubleshooting SSH & IoT Device IP Address Issues & How To Fix