Mastering Secure Remote IoT Access: Transforming IoT Projects With SSH And Beyond
Ever envisioned a world where distance becomes irrelevant, and you can effortlessly manage your IoT projects from any corner of the globe? Secure remote IoT access is no longer a distant dream but a tangible reality. As the Internet of Things continues to evolve, the ability to remotely monitor and control devices has transitioned from a luxury to a necessity. Whether you're a tech enthusiast exploring home automation or a professional overseeing critical infrastructure, the demand for secure and reliable remote access solutions has never been higher.
The Internet of Things (IoT) has reshaped the technological landscape, enabling devices to communicate seamlessly and perform tasks autonomously. However, with this convenience comes the challenge of ensuring security. A compromised IoT device can act as a gateway for malicious actors to infiltrate networks, steal sensitive information, or disrupt operations. To mitigate these risks, secure remote access solutions, such as SSH (Secure Shell), have become indispensable. SSH enables encrypted communication between devices, protecting data during transmission and ensuring only authorized users gain access.
| Category | Information |
|---|---|
| Topic | Remote IoT Device Management via SSH |
| Key Concepts | Secure Shell (SSH), IoT, Raspberry Pi, Remote Access, Security, Tunneling, OpenSSH, Ngrok, Termius, P2P Connections, VPC, Encryption |
| Benefits |
|
| Tools & Technologies |
|
| Security Measures |
|
| Typical Use Cases |
|
| Reference Website | Raspberry Pi Foundation |
The convergence of IoT and remote access technologies has democratized access, empowering individuals with varying levels of technical expertise to manage their devices securely. Tools like OpenSSH, Ngrok, and Termius have simplified the process of establishing encrypted tunnels, eliminating the need for complex configurations such as port forwarding or firewall adjustments. By leveraging these solutions, users can maintain robust security while enjoying seamless connectivity.
- Dominos At Home Copycat Pizza Dough Recipes
- Jeffers Funeral Home Obituaries Services In Greeneville Tn
SSH remains a cornerstone in the realm of secure remote access. This cryptographic network protocol ensures that data exchanged between devices remains confidential and tamper-proof. Its ability to create encrypted tunnels makes it an ideal choice for managing servers, IoT devices, and other computing systems. With SSH, users can securely connect to their Raspberry Pi or other IoT devices without exposing them directly to the public internet, significantly reducing the attack surface.
For those exploring "remote IoT platform SSH Raspberry Pi download free," the process is more accessible than ever. Free and open-source tools are abundant, simplifying the configuration and management of SSH connections. Setting up SSH on a Raspberry Pi involves enabling the service, configuring authentication methods, and ensuring proper security measures are in place. These steps are essential in safeguarding devices against unauthorized access and potential breaches.
Traditionally, remote access required intricate knowledge of IP addresses and firewall settings. Modern solutions, however, have streamlined this process. Encrypted SSH tunnels eliminate the need to expose devices directly to the public internet, simplifying setup while enhancing security. Tools like ngrok facilitate secure tunnels to local machines, enabling users to expose services running on their Raspberry Pi without complex configurations. Similarly, Termius provides a user-friendly interface for managing SSH connections, complete with advanced features such as tabbed windows and command snippets.
- Young Channing Tatum Early Career Iconic Photos
- Gypsy Rose Blanchard From Prison To Freedom What You Need To Know
Remote SSH IoT over the internet has revolutionized the management of smart devices. By leveraging tools like OpenSSH, ngrok, and Termius, users can establish secure and reliable connections without incurring significant costs. These solutions offer unparalleled accessibility, making remote access feasible for tech enthusiasts and professionals alike. The combination of ease of use and robust security features positions SSH as a compelling choice for IoT enthusiasts.
Security remains paramount in the realm of IoT. Following best practices is essential to protect devices from unauthorized access. Avoid using default passwords, enable SSH key-based authentication, and keep software updated. Regularly auditing systems for vulnerabilities and implementing intrusion detection systems ensures a proactive approach to security. Remember, security is an ongoing process that requires continuous vigilance.
Virtual Private Clouds (VPCs) provide an additional layer of security for IoT devices hosted on public cloud platforms like AWS. A VPC creates a private network, isolating devices from unauthorized access. Setting up SSH access within a VPC typically involves configuring a bastion host, which acts as a secure gateway to the private network. This setup enhances security while maintaining accessibility.
OpenSSH continues to serve as the foundation for secure remote access. It enables encrypted connections and robust authentication mechanisms. PuTTY, a popular SSH client for Windows users, offers an intuitive interface for connecting to remote devices. FileZilla, a secure file transfer client supporting SSH, allows seamless file transfers between local machines and IoT devices. These tools simplify the process of managing remote IoT ecosystems.
As the number of IoT devices proliferates, the demand for scalable solutions grows. Organizations must design systems capable of handling increasing numbers of devices and connections without compromising performance or security. Remote SSH IoT over the internet, coupled with VPC configurations, ensures scalability while maintaining robust security measures. This approach is particularly relevant for businesses managing extensive IoT networks.
Peer-to-peer (P2P) SSH for remote access provides a secure method for connecting IoT devices without exposing them to the public internet. P2P connections establish direct communication between devices, enhancing performance and reducing latency. This is particularly advantageous for applications requiring real-time data transfer. Tools like RemoteIoT simplify the setup process, enabling users to create secure networks for their IoT devices.
Securing IoT devices using Raspberry Pi involves implementing secure configurations, robust authentication mechanisms, and continuous monitoring. By following established protocols, users can ensure their projects remain both secure and reliable. The process of securely connecting remote IoT P2P SSH Raspberry Pi downloads involves generating SSH keys, configuring firewall rules, and setting up port forwarding when necessary. Comprehensive documentation and tutorials are readily available to guide users through the setup process.
SSH tunneling is a powerful technique for accessing services running on IoT devices that are not directly exposed to the internet. By using commands such as:
ssh -L local_port:remote_host:remote_port user@remote_server
users can forward traffic from their local machine's `local_port` to the `remote_port` on the `remote_host` through the `remote_server`. This ensures secure access to services while maintaining confidentiality and integrity.
The adoption of SSH remote IoT device free download reflects a growing trend in the tech community. It offers accessible methods for managing IoT devices remotely, addressing the demands of today's interconnected world. Remote SSH for IoT devices ensures projects remain secure while enabling seamless remote access. By encrypting all network traffic, SSH tunnels safeguard data from unauthorized interception.
Setting up a secure remote IoT environment involves a combination of tools and software. SSH clients, P2P solutions like RemoteIoT, and operating system terminals are essential components. Configuring SSH on a Raspberry Pi, coupled with straightforward file downloads on Windows 10, empowers users regardless of their experience level. The convergence of IoT and remote access technologies has revolutionized how we interact with devices, enhancing capabilities and expanding possibilities.
Mastering remote SSH IoT over the internet with AWS introduces scalability as a critical factor for organizations managing extensive IoT networks. Scalable solutions ensure systems can accommodate growing demands without sacrificing performance or security. By leveraging cloud platforms and advanced tools, businesses can efficiently manage their IoT ecosystems.
In today's interconnected world, SSH remote IoT Raspberry Pi free download has gained significant traction among tech enthusiasts and professionals. Whether you're a hobbyist or a developer, understanding how to configure SSH on a Raspberry Pi for remote IoT operations opens countless opportunities. Setting up remote IoT platform SSH access involves configuring SSH, enabling remote access, and selecting appropriate platforms or software solutions.
Secure Shell (SSH) provides secure communication over unsecured networks through encryption. Its tunneling capabilities allow users to interact with services not directly exposed to the internet, enhancing accessibility while maintaining security. Comprehensive guides on SSH remote IoT Raspberry Pi download free for Windows or other platforms typically cover key areas such as installation, configuration, and security best practices. These guides provide step-by-step instructions for using SSH clients like PuTTY and Termius, ensuring users can confidently manage their IoT devices remotely.
Introducing remote IoT VPC SSH involves setting up a Virtual Private Cloud (VPC) on platforms like AWS and configuring SSH access to devices within the VPC. This process includes creating a bastion host, configuring security groups, and setting up SSH key-based authentication. By isolating devices within a private network, users enhance security while maintaining accessibility.
Mobile access to IoT devices has become increasingly important, with many users seeking to monitor and control their devices from smartphones or tablets. Securely connecting remote IoT P2P SSH download on Android involves installing SSH client apps like Termius or JuiceSSH and configuring connection settings. Security considerations are paramount when accessing IoT devices from mobile devices, as these platforms are often more vulnerable to malware and other threats.
Securing remote IoT access is a multifaceted endeavor requiring a deep understanding of networking principles, security best practices, and available tools. By following established guidelines and adapting to evolving threats, users can confidently manage and monitor their IoT devices from anywhere in the world. The journey to secure remote access empowers users to unlock the full potential of IoT while ensuring their systems remain protected.
- Myrtle Beach Inmate Search Public Records Access Info Online
- Dwight Howard Kids Wives Family Life Get The Inside Scoop

SSH Client SFTP Terminal and Telnet Free download and install on
How to Connect to a Remote Server Over SSH on Windows Linode Docs
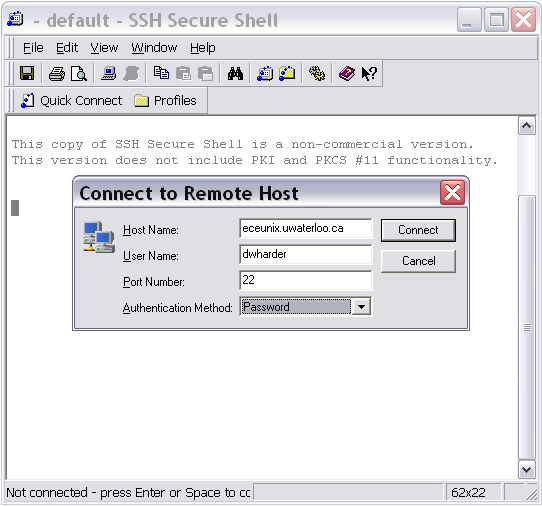
SSH Secure Shell Client MTE 241 University of Waterloo